With malicious software such as WannaCry and Petya causing havoc on PCs and laptops, we are currently witnessing yet another cyber-threat, this time on mobile devices that goes by the name of CopyCat malware.
Expected to be the one of the biggest and most widely spread Android based cyber attacks, affecting more than 14 million Android devices worldwide, the CopyCat malware is reported to enter an Android device via a third-party source or through a source of phishing.
Once in, the CopyCat malware automatically downloads a toolkit and is able to root the Android device thereby gaining complete control over it. Following this, the malware can install fraudulent apps and display fraudulent ads. These tactics have generated a large amount of profit to the creators of CopyCat.
Enterprises would be the most affected by such cyber attacks, since it involves the risk of losing sensitive corporate data residing on an employees' Android device. History has shown us that company data in the wrong hands can topple even the largest of organizations. In such a case, it is better to be equipped to take on such threats, rather than face their aftermath.
Given that the malware has been spreading at a rapid rate, infecting millions of devices, it is essential for enterprises to take preventive action against such threats, especially since there is a risk to corporate information.
Here's what should be done to protect your enterprise:
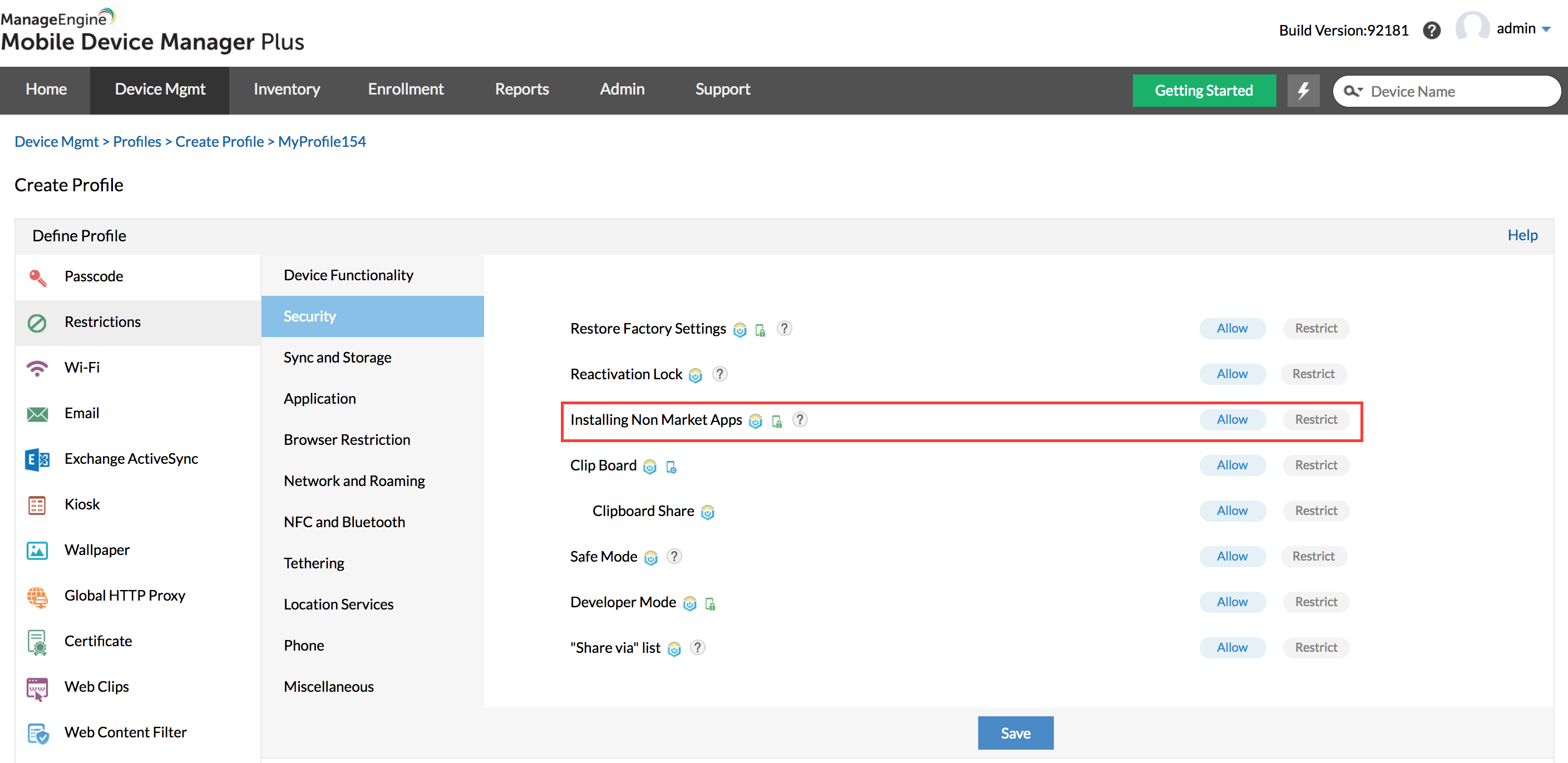
Disable installation of non Playstore apps:
Since one of the points of entry for the CopyCat Android malware is through a third party app source, enterprises can set policies to restrict devices from downloading applications from a third party source.
This seems to be an easy task on an individual device, but considering the number of mobile devices being used in an enterprise, it can be cumbersome to individually perform this and ensure that the policy is enforced.
This is simplified using ManageEngine's Mobile Device Manager Plus. Policies can be set and enforced onto as many devices as required immediately.
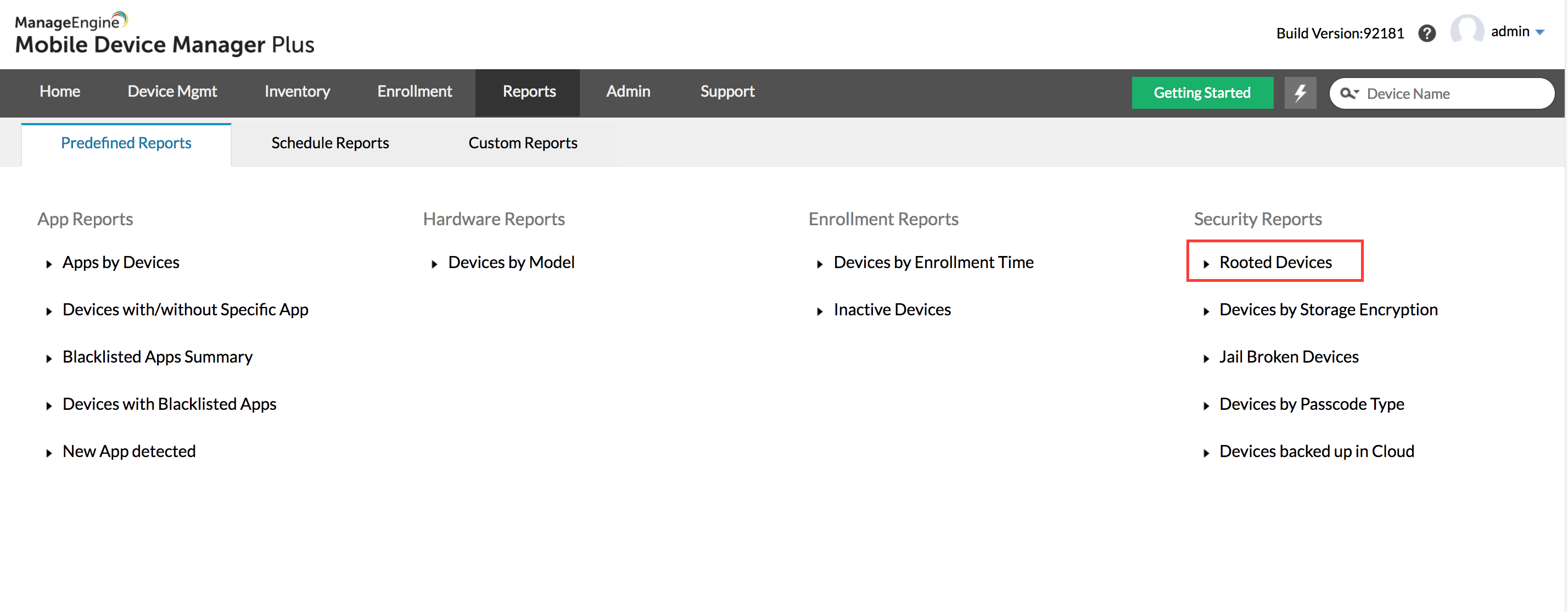
Jail broken iPhones and rooted Android devices always pose a greater risk to enterprise security since they are an easier target for malware and cyber attacks.
In the case of the CopyCat Android malware, once infected, the device gets rooted, and is taken over by the malicious code. Chances that the infection spreads within a network is high.
Using Mobile Device Manager Plus, detection and reporting of rooted Android devices can be done immediately.
Once you are able to detect the device that is rooted, you can perform a variety of actions on it, some of which include completely wiping the device data, selectively wiping the corporate data residing on the device and removing the device from the corporate network in order to avoid further damage caused due to spreading of the malicious code.
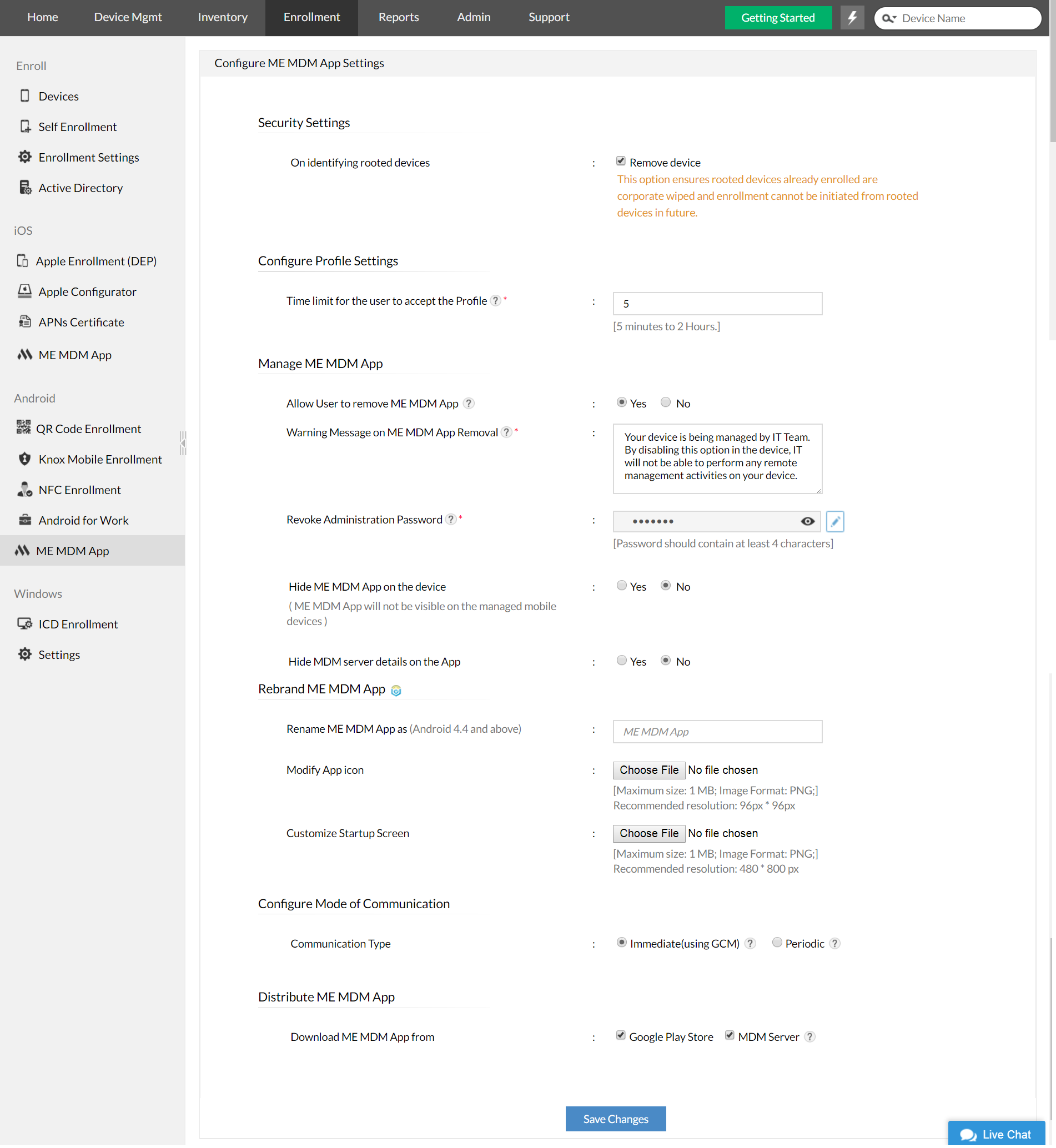
Equip your enterprise with ManageEngine Mobile Device Manager Plus to ward off any form of cyber attacks.